There is a cyber-attack somewhere in the world every 39 seconds, and since 2013, hackers have stolen 3.8 million records daily.
With this number only going up, no organization can claim that they are immune to cyber-attacks. They can, however, deploy strong data security controls to protect their confidential data from bad actors.
The practice of determining what data in a company’s system can be shared with third parties is called data privacy. The concept is very similar to data security which aims to protect a company’s data against malicious threats, but the two still differ. Just because data is private, it isn’t always secure against hackers who can find other ways to make the data inaccessible or even delete it altogether.
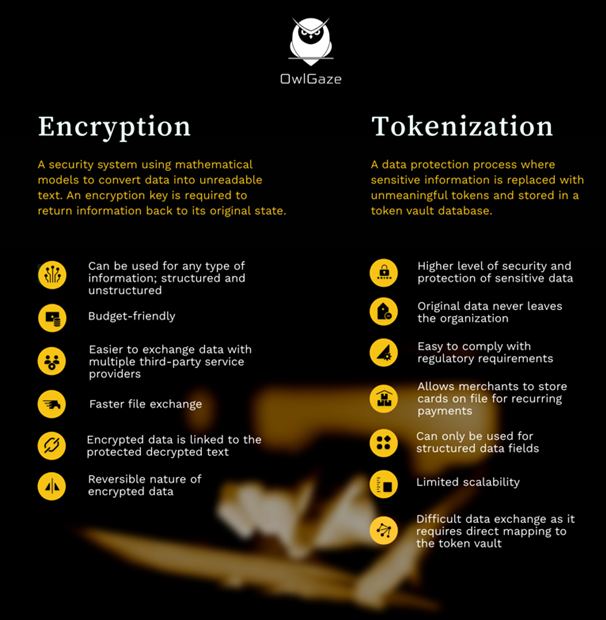
A common practice to ensure firmwide data privacy is encryption. It involves converting data into a random sequence of symbols using an encryption key. The data can be converted back into its original form using a decryption key. However, as the research on cryptography has advanced, hackers have found new ways to decipher encrypted data using cryptanalysis techniques. These techniques either intercept encrypted communication or derive the encryption key by understanding the key-building algorithm in detail.
Encryption is reversible, but tokenization is irreversible
Besides advancement in cryptanalysis techniques, the biggest challenge with encryption is that the encrypted data is directly connected to the decrypted text it is protecting. This way, the hacker knows that the visible gibberish will eventually make sense once the data is decrypted.
To add an extra barrier between the hacker and the confidential data, tokenization is adopted.
Tokenization, as the name suggests, is a process where confidential information is represented as a token that acts as a placeholder for the actual information. It contains meaningless data generated randomly. Even if the hacker gets to know the data on the token, they wouldn’t be able to use an algorithm to decipher the data because it is not connected to the confidential information. A secured table is created which maps tokens to the confidential information it is protecting. To retrieve the information, the token needs to be exchanged on the tokenization software, which then decrypts the data to reveal the confidential information. Tokenization has risen to popularity within companies that hold large amounts of personally identifiable information (PII), including financial and healthcare institutions.
Cost, Compliance, Risk: Factors to keep in mind before deciding the right technique for your organization
Tokenization is more secure, but encryption is cheaper, so which technique best suits your organization? To find out, we need to answer four questions:
- Is your industry prone to cyber-attacks?
Cdnetworks reports that healthcare, government, energy, higher education, and small businesses are the most vulnerable to cyber-attacks in 2021. Such industries should adopt tokenization as it offers a higher level of security. - How many third-party service providers do you work with?
With tokenization, third parties would require double access to the token vault and a secure table that maps token values to actual data, making the process complex. Companies that work with many third parties will find it easier to use encryption over tokenization. - What is your IT security budget?
Tokenization is more sophisticated than encryption, but it comes at a much higher cost. Companies should perform a cost-benefit analysis on the data they need to protect. - What data privacy laws do your company need to follow?
Organizations accepting card payments need to comply with PCI security standards which classify even encrypted data as sensitive information since it is reversible. Companies would need to spend on additional security tools to secure their encrypted data further. Companies in industries required to comply with stringent security standards, especially in the financial sector, should choose tokenization due to cost-effectiveness and scalability.
Answering these questions will bring you closer to finding the best data privacy technique for your firm. Other data privacy considerations, including privacy governance, data lifecycle mapping, privacy impact assessment, data incident management frameworks, etc., go into making a well-rounded data privacy plan.
For more information and inquiries about cybersecurity insights, contact us at info@owlgaze.com
Authors:
Ralph Chammah | Chief Executive Office – OwlGaze
Image sources: Freepik.com