Digitization of healthcare
The digitization of healthcare has led to the proliferation of numerous resources and tools to facilitate healthcare practices and patient experience. Accessibility of health information is one of the tenets of healthcare services today that defines the ultimate healthcare experience – the one that captivates the world with a seamless user experience.
Waiting for a ring on your phone or visiting the clinic for reports is now considered old fashion. All the results are now inter-connected with your online health profile. It consists of sensitive patient records and details of healthcare services — making this information particularly vulnerable.
With this increased vulnerability, cybersecurity for healthcare providers becomes all the more important. Personal health information is 50x more valuable than financial information.
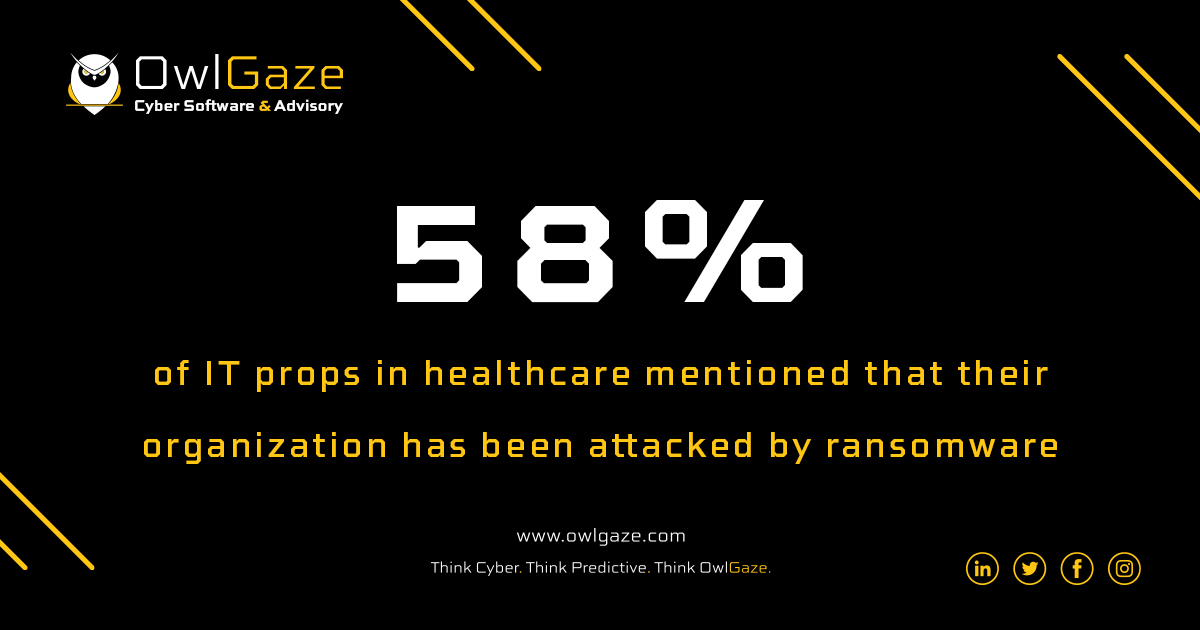
Reports suggest that cyber-attacks in the healthcare sector increased by 42% in 2020. During the overwhelming rise in COVID-19 infection with hospitals managing patient care with limited resources, data protection measures of many hospitals crumpled.
The chaotic nature of this pandemic has created opportunities for hackers to steal patient information. To prevent this damage, the healthcare sector needs a renewed focus on cyber security measures that protect critical healthcare data.
Hospitals play a crucial role in patient care and are considered critical infrastructure that is responsible for transporting medication, blood products, lab samples and other materials to patients across the entire healthcare ecosystem.
Important assets of the healthcare sectors – The primary targets
Patient’s health records: Healthcare facilities are repositories of vast amounts of data — patients’ private information. The nature of the data, such as personal health information (PHI) and credit card numbers, makes the healthcare industry a prime target of cyber-attackers.
Healthcare services: Cyber-attacks can hamper the delivery of healthcare services. With many of these services being time-sensitive, a network disruption can cause delays that jeopardize lives.
Reputation: Cyber-attacks tarnish public images. Any breach can damage a healthcare provider’s reputation, which can irreparably impact the trust, which is so crucial when choosing which provider to place yourself or your loved ones in the care of.
Cyber threats in the health sector
Cyber-attacks are of varied nature; however, the common ones prevailing in the health sector are:
Email phishing attacks: Phishing attacks are masqueraded as messages from legitimate or trusted sources. With the motivation to solicit critical information or breach the system with malicious software, hackers usually provide links or files for the user to access, leading to data compromise.
Malware: Malware of varied categories — Trojan, virus, spyware, botnet, worm, ransomware, and zero-day exploits — disrupts a computer’s normal behavior and provides attackers the power to breach the system in several ways. Malicious file installation can lead to information exfiltration, infection of the system, or unauthorized access.
Theft of equipment, loss of data, and insider threats: Losing everyday devices such as mobile phones, laptops, and USBs poses immense risk to the safety and wellness of people. Health information is sensitive and can cause significant damage to an individual or a country. Additionally, insider threats from lost devices can be both accidental and intentional.
Ignorance and lack of concern: Large-scale ignorance and lack of concern regarding basic security practices strongly contribute to vulnerability threats. In the healthcare industry, these basics, such as changing passwords and ensuring devices are secured, may be overlooked in favor of convenience in the midst of a fast-paced environment.
The Cyber Security Essentials
Step 1: Create and maintain an updated IT inventory
Creating and maintaining updated IT inventories of all assets helps in the detection of cyber risks and threats. Non-corporate devices such as personal cell phones might also have vulnerabilities that can be exploited. Hence, it is advised to maintain a record of all kinds of devices — hardware, software, and medical devices — connecting to the corporate IT network.
Healthcare providers should ensure frequent updates of asset inventory, such as new hardware purchases and decommissioning, and further maintain records of device details to facilitate patching of potential critical vulnerabilities.
Step 2: Secure data – Be proactive, not reactive
Technology: Implementing solutions and practices, such as using a privileged access management (PAM) tool, implementing multi-factor authentication (MFA) checks, scheduling security patches, and advance endpoint protection (EPP) software, can restrict malicious behaviour automatically. Monitoring your network, correlating your security logs, and maintaining regular backups are fundamental security practices.
People: Educate employees and raise awareness regarding cybersecurity. Training sessions to cultivate cyber hygiene practices such as logging out of applications, devices, and password security management are essential in the fight against cyber threats.
Process: Outsourcing and vendor management should be managed appropriately. Employees should be educated to inform on suspected cyber incidents and follow a standardized protocol.
Step 3: Implement cyber security measures
Organizations should make sure that cyber security policies and standards are designed from an overarching strategy that encompasses all their needs and then implemented accordingly. Staff should know the appropriate steps to follow to raise an alarm about any suspicious activity. In addition to regular employee education, a dedicated incident response team should be in place.
According to the Wall Street Journal, amid this pandemic, cyber-attacks in the healthcare sector incessantly increased in 2020. It is predicted that each month last year more than 1 million people were impacted by data breaches at healthcare organisations.
To prevent any further damage, organizations should adopt industry best practices that halt these crimes in their tracks.
The best time to integrate cybersecurity measures in your company is now.
For more information and inquiries about cybersecurity insights, contact us.